CVE-2023-40810-HTML injection-Product Creation

Vendor of the product(s) –
- Product Name – OpenCRX
- Version – exact ver of the product which is vulnerable – 5.2.0
- Affected component(s) – Product
- Attack vector(s) – Web Application
- Suggested description of the vulnerability for use in the CVE- HTML injection on the Product Creation
- Discoverer(s)/Credits – Nandini Sharma
- Step by Step POC written in sequential order – prepare a word file for all this.
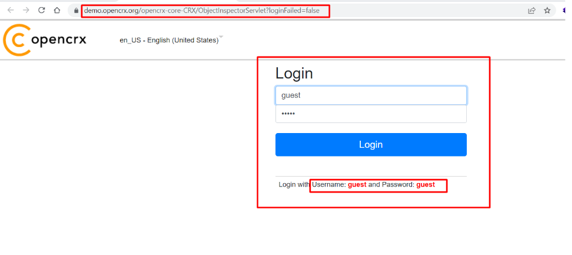
Step-1 Navigate to https://demo.opencrx.org/opencrx-core-CRX/ObjectInspectorServlet?requestId=3D06QMASG8CMLDTV63YISTS8F&event=24?loginFailed=false and login as Guest credentials
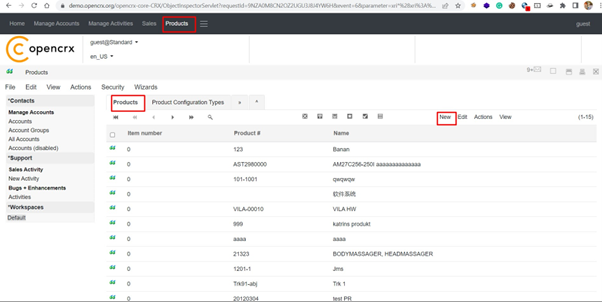
Step-2 Now, create new Product in the Product Section as shown below: –
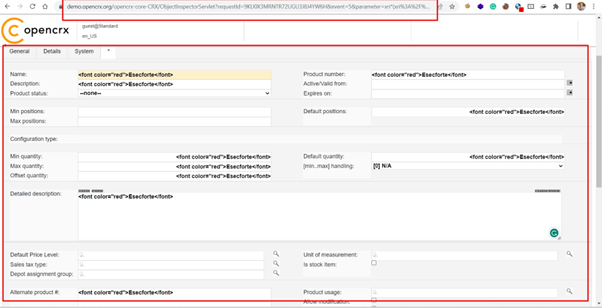
Step-3 Now, Insert Html payload in the Name field as shown below:-
Paylaod – eSecforte
Note: All the fields in general are vulnerable to HTML Injection
Step-4 Now, click on the save button to save this. It has been observed by the auditor that HTML payload execute successfully.
Note: Following are the vulnerable fields.
Name,
Product Name,
Detailed Description,
Reason,
Category,
External Link

[Discoverer]
Nandini Sharma from eSec Forte Technologies Pvt. Ltd


More Insights