XM Cyber Breach & Attack Simulation
XM Cyber Breach & Attack Simulation enables enterprises to continuously simulate attacks, uncover hidden vulnerabilities, and prioritize remediation based on real risk exposure—strengthening security posture before real threats strike.

What is XM Cyber Breach & Attack Simulation
XM Cyber is a breach and attack simulation (BAS) platform that provides continuous visibility into security gaps by emulating multi-stage, real-world attacks. It identifies hidden vulnerabilities and misconfigurations across hybrid networks and validates the effectiveness of security controls, delivering actionable, risk-based recommendations.

XM Cyber Breach & Attack Simulation Features
Continuous Security Validation
24/7 simulation of attack scenarios.
Hybrid Environment Coverage
Supports on-premises and cloud networks.
Automated Risk Prioritization
Focus on vulnerabilities with highest real-world impact.
Real-World Attack Simulation
Emulates tactics, techniques, and procedures (TTPs) used by actual attackers.
Attack Path Visualization
Clear visual representation of potential attacker movement and privilege escalation.
Integration with Existing Tools
Seamlessly works with SIEM, SOAR, and vulnerability platforms.

XM Cyber Breach & Attack Simulation Services
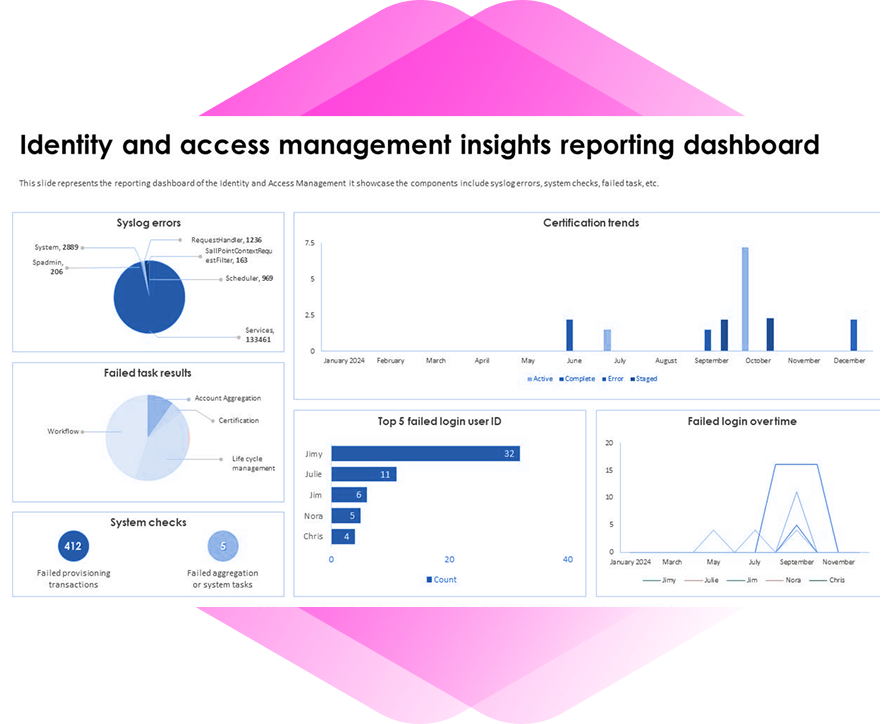
XM Cyber provides a suite of services to ensure effective deployment and utilization:
- BAS Deployment – End-to-end setup tailored to client environments.
- Attack Path Analysis – Examine lateral movement paths and escalation risks.
- Customized Threat Modeling – Create organization-specific attack scenarios.
- Integration & Automation – Embed XM Cyber into enterprise security infrastructure.
- Training & Support – In-depth team training and ongoing technical guidance.
Key Benefits
Reduce Risk Exposure – Identify and eliminate attack paths before exploitation.
Prioritize Remediation
Focus efforts on vulnerabilities threatening critical assets.
Improve Incident Response
Understand real attack vectors to strengthen response.
Enhance Security Posture
Continuous validation drives consistent defense improvement.
Save Time & Resources
Automate simulations and obtain actionable insights efficiently.

Related Resources