ZecOps Mobile Security
Automated Mobile DFIR Platform to Detect, Investigate & Respond to Sophisticated Mobile Device Compromises
ZecOps Mobile Security provides the only forensic-grade solution to extract, deliver, and analyze mobile device logs for signs of compromise or malicious activity—a must-have tool for modern mobile threat detection and response.

ZecOps Mobile Security: Overview
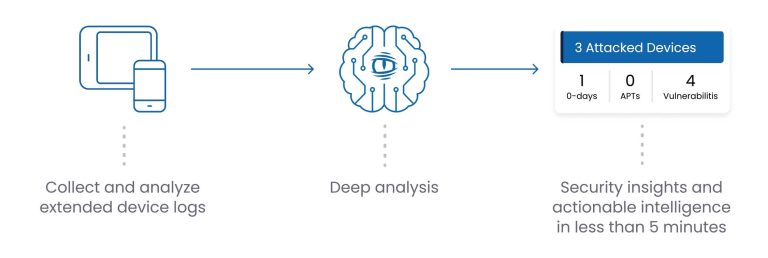
ZecOps empowers security teams to detect mobile cyber incidents by automatically collecting device logs and identifying indicators of compromise. It offers an end-to-end mobile incident investigation solution—from log extraction via collectors to automated timeline generation—ensuring visibility into mobile threats that traditional tools often miss.
Inspect your devices wherever they are
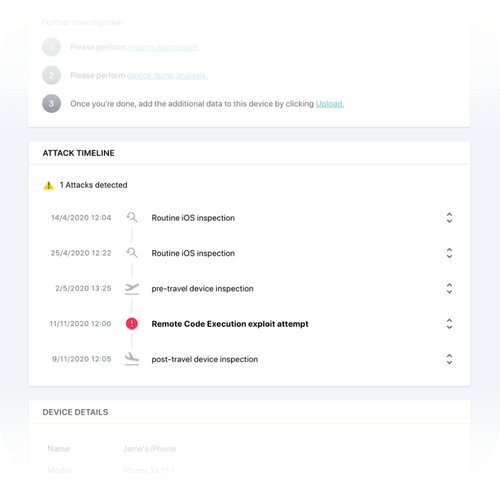
Inspect Your Devices Wherever They Are Deploy the ZecOps Collector as a lightweight agent on Windows or macOS (or via a secure kiosk) to automatically or on-demand gather relevant mobile logs. Streamline Incident Response Build automated incident timelines that map suspicious behavior on mobile devices, supporting clear incident narratives and stakeholder reporting.
Streamline your incident response
Deploy Widely and Securely ZecOps operates on-premise or in cloud environments, enabling broad deployment without compromising user privacy. Enable Threat Hunting Empower SOC and CERT teams with tools to analyze beneath app sandboxes, craft custom YARA rules, and drive advanced mobile threat hunting.
Deploy widely and securely
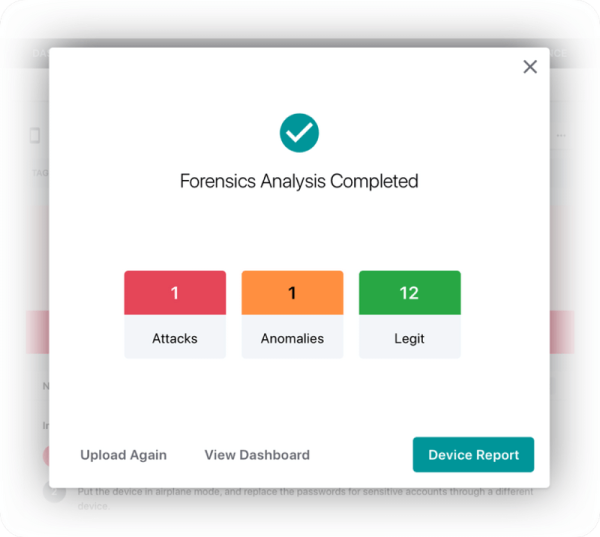
Secure Deployment Options: Assisting with on-premise vs cloud deployment to fit organizational policies and privacy requirements. Reporting & Forensic Documentation: Customizing incident report templates and providing timeline-based forensic outputs.
Enable threat hunting
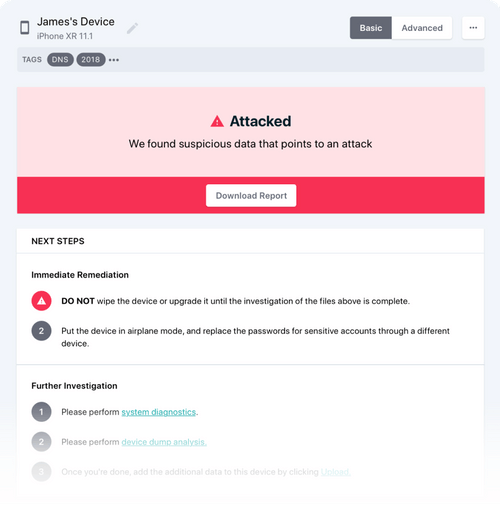
Incident Response Enablement: Guiding SOC and DFIR teams in mobile log collection, analysis, and threat identification. Threat Hunting Training: Enabling advanced usage—including YARA rule creation and anomaly detection.
Get the Results That Matters
- Discover Attacks Using Mobile IOCs
- Streamline Your Incident Response
- Deploy Widely and Securely
- Inspect Your Devices Wherever They Are
These services ensure you can operationalize ZecOps for scalable mobile DFIR support in enterprise environments.
Industry Insight: Surge in Mobile Threats Demands Forensic-Grade Visibility
ZecOps stands out by empowering security teams to uncover zero-click and zero-day mobile attacks that traditional monitoring tools often miss. It’s now integrated into enterprise DFIR workflows following its acquisition by Jamf in 2022. 60% of organizations reported mobile devices were involved in a security breach in the last 12 months. Zero-click attacks and mobile-targeted zero-days increased by 466% in the past two years, highlighting the urgent need for automated mobile DFIR platforms.
More Insights
IBM Security Verify Pricing
Its cost is dependent upon the license you wish to choose as it gives you various options. The detailed price structure can be availed through Value Added Distributor eSec Forte Technologies who are well versed with all the data associated.