Zimperium Mobile Application Protection Suite (MAPS)
End‑to‑End In-App Security Platform Protecting Android & iOS Apps from Dev to Runtime

Zimperium Mobile App Protection Suite : Overview
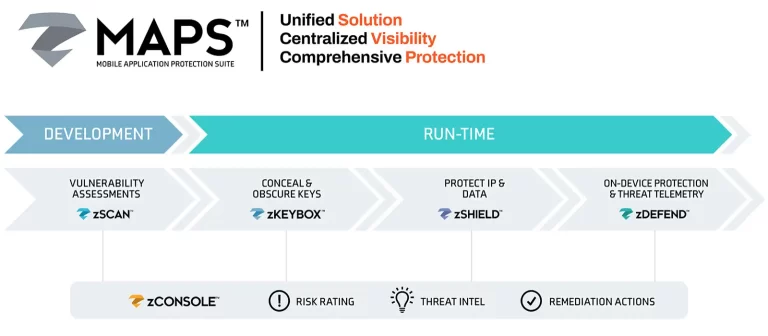
Zimperium’s Mobile Application Protection Suite (MAPS) is the only unified platform that integrates mobile application security testing (MAST), runtime protection (RASP), cryptographic key protection, and application shielding—all delivered via a centralized threat dashboard. It offers continuous, inside-out and outside-in protection across the app lifecycle: from scanning during development to self-defending capabilities on user devices. MAPS ensures apps are secure, compliant, and resilient—even on unsecured networks or weakened endpoints.
Why Zimperium MAPS ?
Mobile Application Security Testing (zScan)
Detects and remediates security, compliance, and privacy issues early in development before apps are deployed.
Application Shielding (zShield)
Provides advanced protections like code obfuscation and anti-tampering to prevent reverse engineering and safeguard IP and internal data.
Runtime Protection (zDefend / RASP)
On-device defenses using machine learning to detect and block malware, phishing, network attacks, and tampering—even offline.
Key Protection (zKeyBox)
Implements white-box cryptography to secure encryption keys and sensitive data from extraction or manipulation, even under attack.
Centralized Threat Dashboard
Allows real-time visibility into security events and enables responsive policy enforcement without requiring app updates.

Services Offered by eSec Forte
Zimperium Mobile App Protection Suite Pricing
Its cost is dependent upon the license you wish to choose as it gives you various options. The detailed price structure can be availed through Value Added Distributor eSec Forte Technologies who are well versed with all the data associated.
More Insights
IBM Security Verify Pricing
Its cost is dependent upon the license you wish to choose as it gives you various options. The detailed price structure can be availed through Value Added Distributor eSec Forte Technologies who are well versed with all the data associated.