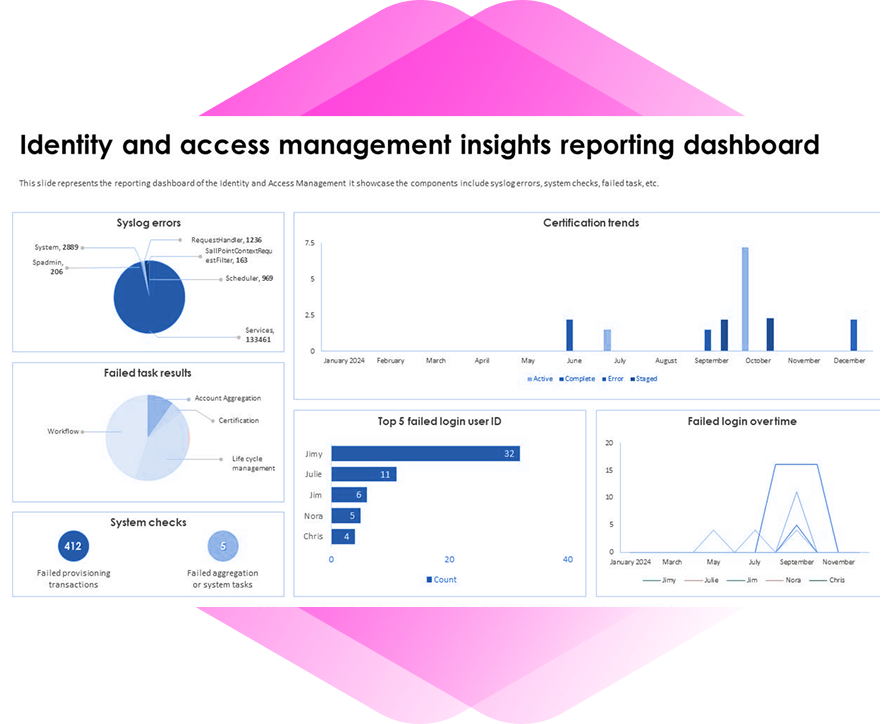
IBM Security Verify – AI-Driven, Cloud-Native Identity & Access Management (IAM)
IBM Security Verify delivers scalable, AI-powered identity management for workforce and consumer access. It provides secure authentication, SSO, MFA, adaptive access, and governance across cloud and on-premise environments.
What is IBM Security Verify?
IBM Security Verify is a modern IAM solution designed to secure both workforce and consumer identities. The cloud-native, continuously delivered platform centralizes user management, enables adaptive authentication, supports passwordless access, and provides governance capabilities. Acting as an authentication broker, it facilitates rapid application onboarding via standard protocols (OIDC, SAML 2.0) and delivers context-aware, risk-based access decisions powered by AI.

Key Features
Single Sign-On (SSO)
Seamless access to hundreds of applications via OpenID Connect and SAML 2.0 connectors.
Multi-Factor & Passwordless Authentication
Supports OTP (SMS/email), push approvals, biometrics, FIDO2/WebAuthn, and knowledge-based authentication.
Risk-Based Adaptive Access
Context-aware policies using device fingerprinting, IP geolocation, behavioral analytics, and Trusteer integration.
Centralized User Governance & SCIM Provisioning
Manage user attributes, relationships, and SCIM 2.0 inbound/outbound provisioning.
Consumer Identity Capabilities
Secure customer registration, profile management, cross-identity linking, and social login integration.
Continuous Delivery & Cloud Deployment
Cloud-native architecture with instant access to updates and hybrid deployment flexibility.

Services by eSec Forte
- Solution Assessment & Planning – Evaluate IAM posture, define strategy, and plan workforce and consumer identity transformation.
- Solution Design & Deployment – Configure SSO, MFA, adaptive access policies, and user governance workflows.
- Integration & Customization – Support integration with legacy apps, custom SSO flows, Trusteer, and SCIM provisioning.
- Training & Enablement – Hands-on operational training for administration, policy configuration, and analytics.
- Managed IAM Support – Continuous operational support, configuration management, analytics tuning, and incident handling.
- Compliance & Governance Auditing – Assistance with policy certification, audit reporting, and regulatory alignment.
Key Benefits
Cloud Code Security
Scan IaC, container images, serverless functions, and secrets early in CI/CD pipelines; integrate findings for pre-deployment remediation.
Cloud Security Posture Management (CSPM)
Continuously assess cloud configurations, detect misconfigurations, and enforce policies during and before deployment.
Cloud Workload Protection (CWP)
Runtime monitoring and threat detection for hosts, containers, and serverless workloads, including anomaly-based defense.
Cloud Network Security
Identity-aware micro-segmentation, traffic log analysis, and layer-7 threat prevention for cloud-native networks.
Cloud Infrastructure Entitlement Management (CIEM)
Discover and govern cloud identities, manage excessive privileges, and detect anomalies using UEBA.

Related Resources