Tenable SecurityCenter
Enterprise-grade, on-premise vulnerability management that offers risk-based prioritization, advanced analytics, and real-time visibility across assets and threats to improve decision-making, remediation, and compliance readiness.
.png)
What is Tenable SecurityCenter?
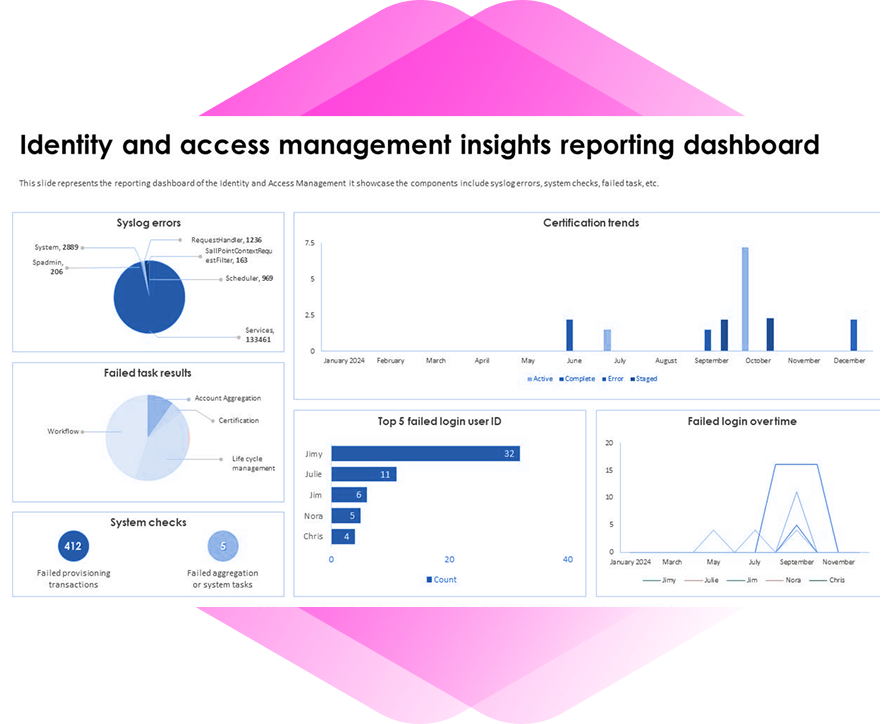
Tenable SecurityCenter delivers an integrated, on-premise solution for managing vulnerabilities across complex IT environments. Leveraging active scanning, agent data, passive network monitoring, and external attack surface discovery, it centralizes intelligence across the enterprise. With comprehensive dashboards, analytics, and automation, the platform enables security teams to identify, prioritize, and remediate vulnerabilities efficiently while supporting audits and compliance objectives.

Key Features
Comprehensive Asset & Vulnerability Visibility
Consolidates data from Nessus scanners, passive sensors, agents, and external attack surface discovery to provide real-time visibility.
Risk-Based Prioritization
Uses threat context, predictive risk scoring, CVSSv4/EPSS metrics, and business impact to prioritize remediation efforts.
Advanced Analytics & Reporting
Hundreds of pre-built dashboards and customizable reports for vulnerability trends, compliance tracking, and operational risk insights.
Distributed Scanning Support
Manages multiple Nessus scanners, passive monitoring agents, and scanning zones for efficient coverage.
Log & Event Correlation
Enables advanced searches and cross-system correlation to unify security events and alerts.
Policy & Compliance Automation
Generate audit-ready reports aligned with PCI-DSS, HIPAA, ISO 27001, NIST CSF, and CIS benchmarks.

Services by eSec Forte
- Platform Deployment & Configuration – Tailored installation and configuration of SecurityCenter and scanning infrastructure aligned with organizational IT architecture and risk profile.
- Asset & Policy Mapping – Define scan zones, classify assets, configure prioritization policies, and align risk scores with business criticality.
- Dashboard & Report Customization – Create tailored dashboards and automated reporting workflows for operational and audit requirements.
- Training & Enablement – Workshops on scan design, triage, remediation workflows, and compliance reporting for security teams.
- Continuous Optimization Support – Managed services including scanner health checks, rule tuning, remedial feedback, and integration enhancements.
Key Benefits
Real-Time Vulnerability Intelligence
Unified visibility across active, passive, and agent-based scans ensures no asset or threat vector is overlooked.
Focus on What Matters
Risk-based scoring prioritizes high-impact exposures, reducing unnecessary effort chasing low-risk vulnerabilities.
Accelerated Remediation Workflow
Automated alerts, reporting, and policies streamline response and reduce time-to-fix.
Audit-Ready Compliance
Built-in reporting templates and standards mappings simplify certification and audit processes.
Scalable Enterprise Architecture
Supports large distributed deployments with hundreds of scanners and centralized management.

Related Resources